Internet Security Fundamentals - Online Edition
3 Vulnerabilities & Security Flaws
There are millions of lines of programming code behind a modern computer system, and it is so complicated that mistakes are made, or features are added without considering if they could be used maliciously. These mistakes or flaws when used to access areas they were never meant to or use software features in ways they were never intended are known as vulnerabilities.
Malware that uses security flaws known as vulnerabilities in your operating system or other installed software such as Java or Flash, is sometimes called a drive-by download or zero-day attack. Nothing can really protect you from security exploits, but once they are known some antivirus systems can protect you. For everyone else, it's a waiting game for the security patch or fix to be deployed. It's a bit like having a car that has a flaw that causes the alarm to deactivate and the windows to open, if a certain action or sequence is performed. Once the thieves know about this flaw, your car is more likely to be broken into. This may sound far-fetched, but the car on my driveway has been broken into twice like this.
Hacking or tricking mainstream high traffic websites into redirecting users to malicious software is also an effective way of distributing malware. As the website is familiar and trusted, people are more easily caught off guard, with prompts asking them to agree to something or they are exposed to an automated exploit kit. It’s also not uncommon, the TV chef Jamie Oliver’s website was compromised 3 times in 2015.
So, you can have a fully patched machine, with the latest anti-virus software, stick to only mainstream websites and still end up with a virus due to just bad luck. The mainstream website may have been hacked, and via a new security exploit your machine is compromised. According to Google's Official Blog, in 2015 they blocked over 780 million bad adverts. This included over 7000 phishing sites, 17 million adverts designed to look like system warnings to trick people into clicking them and 10,000 sites offering unwanted software. Sometimes stuff slips through the net and at one point, the Yahoo search engine was in the news after it was tricked into displaying malicious advertisements to thousands of people which redirected users to a webpage hosting an automated exploit kit. This checks for various vulnerabilities on a user’s computer (in a matter of seconds) and can install a mix of Trojans and viruses once a vulnerability is found. These exploit kits are sold to criminals by other criminals, as an online monthly service, so the amount of technical knowledge required be the criminal is a fraction of what it used to be. They are constantly updated with new features to improve infections rates and avoid detection by security software and are becoming a major money earner for the criminals.
According to the Common Vulnerabilities and Exposures (CVE) program at www.cve.org, which identifies, defines and catalogs publicly disclosed cybersecurity vulnerabilities, there are 225,772 CVE recorded vulnerabilities since September 1999, of which 29,065 were in 2023 alone. Security software patches are often released within 24 hours of the vulnerability being disclosed, so you can see just how important patching and updating your software is. For information on vulnerabilities, see the Threat Reports section in the Further Reading & Resources chapter at the end of this eBook.
Also, vulnerabilities can be in mainstream systems and software for years. You may have heard of the heartbleed and shellshock bugs which have recently been in the news. These major flaws have only recently come to light, despite the shellshock bug being 20 years old. Bounties worth thousands of dollars are offered to people who report these bugs by most of the major internet companies like Google, Facebook and Microsoft. Once the right companies are aware of the bugs, they can do something about it and issue updates and patches. To help address the problem Google launched Project Zero in July 2014, with a team of security researchers tasked with improving security across the internet and not just for Google products. So, while it may not seem it, the internet does get a little bit safer every day.

Recently there has been a resurgence in macro-enabled office files like the one above arriving by email, which use the scripting feature to automate functions in a malicious way. Make sure all your Microsoft Office or equivalent programs are not set to run macros automatically when you open a document. In Microsoft products this can typically be found under FILE – Options – Trust Center – Trust Center Settings. In a business setting, change the Macro Settings to Disable all macros with notification, to enable you to choose to run a legitimate macro. For home use, you can change it the highest setting Disable all macros without notification.
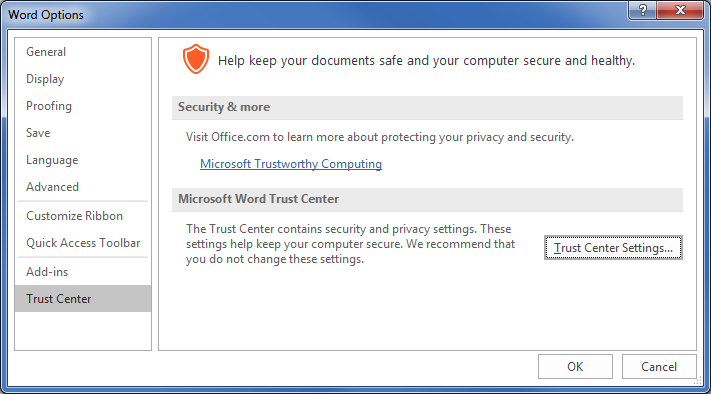

Also, while you are in the Microsoft Office Trust Center, go to Protected View and check that everything is ticked.

Protected View is a rather annoying but highly useful security feature in the Microsoft Office suite, which delays you editing any documents that someone may email you or ask you to download. By opening them in a read only protective environment any malicious scripts embedded in the document will not run. This allows you to make a judgement call on whether the document is genuine and if you need to edit it, click Enable Editing in the yellow bar at the top of the document. If you do not need to make any edits or changes, it is best to stay in the Protected View environment.

Unfortunately, if you want to print a document, you have to drop out of Protected View, so please make sure you completely trust the sender or the source of the document. If you are unsure, do not print it and try to just read it onscreen. If you believe your document may be malicious or untrustworthy, simply close the document and delete the file. Once you drop out of Protected View and enable editing, the next time you open the same document, it will not prompt you again, even if you didn’t make any changes.

Macro Security settings for Apache OpenOffice or LibreOffice, is under:
TOOLS – Options – OpenOffice/LibreOffice – Security – Macro Security

This is an example of a high quality fake fixed penalty email with a macro enabled word file.
It appears to be from the Driver and Vehicle Standards Agency (DVSA) and via their secure email system gsi.gov.uk which shows you how easy it is for criminals to fake an address.

As many people now have macros turned off as a default security measure in Microsoft Office, the criminals have adapted their tactics. They know they have to get you to manually turn the macros back on and as a result will try to trick you into doing so. In the example below the gibberish text has actually been typed in like that and has nothing to do with ‘data encoding’. Turning on macros will not make the text readable, unless the criminals have programmed the macro to replace the text with something else, as well as download and run their virus or open a website that hosts an exploit kit. So be wary of any attachments that contain a macro, as generally there is little reason to send someone a file containing one and you would never need to enable a macro to see what is in the document.

Please note that the following Office file types can contain macros:
.doc .xls .ppt .rtf .docm .dotm .xlsm .xltm .xlam .pptm .potm .ppam .ppsm .sldm
To make matters worse, the criminals also have their own versions of online scanning services which can check if their viruses or malicious web links will be detected by a range of antivirus solutions, without any of the information being passed on to the antivirus companies. Anything that fails the test is modified or tweaked until it passes, giving the criminals a window of time where their malicious payload stands a good chance of being delivered. The cost of one of these services was less than $0.15 per submission or $30 for a monthly unlimited subscription.

This is an example of a fake email advert designed to trick you into visiting to a malicious site. So be on the lookout for bogus marketing emails with fake ‘unsubscribe links’, remember as they can look entirely genuine, the safest thing to do is never follow links from an email.
In December 2021, major vulnerabilities were found in a Java-based logging tool called Log4j used by millions of online servers worldwide. The vulnerabilities allow attackers unauthorised access to systems, to infect networks, steal credentials and other data, combined with the ease of exploiting the vulnerabilities, making this one of the worse ever on record.
Log4j is included as an open-source software library in many other systems. Open-source software is deemed to be safer than normal ‘closed’ source copyrighted software, as there are potentially thousands of programmers looking at the code base to spot flaws and bugs. Unfortunately, it is a double-edged sword as the criminals can also look at the code base to spot flaws and bugs. The vulnerabilities have now been patched (or are in the process of being patched) so it is important to install software security updates for all systems to benefit from these fixes as quickly as possible. Log4j is just one example, it probably won’t be the last.
For more information on Log4j see the UK National Cyber Security Centre’s post:
https://www.ncsc.gov.uk/information/log4j-vulnerability-what-everyone-needs-to-know
Please understand that the only completely secure computer is one that is turned off with the power cord unplugged and also the battery taken out (for laptops). There is no such thing as a secure computer that is connected to the internet; all you can do is reduce the risks. The same way you reduce your risks when living in a modern city, by avoiding certain areas at night. There are risky places in a city and on the internet. The illegal software site is probably not going to play fair, the same way someone selling stolen goods may by giving you nothing more than an empty packaging box that weighs the same as the original.

So, every time you go online there is a very slim chance that you could fall victim to a piece of malicious software, and you will be powerless to stop it, though you’d probably never know it was there. Protect yourself as much as possible by carrying out the steps throughout this eBook, and make sure all your software is updated regularly. Some common software to check includes:
Microsoft Windows 10: Start - Settings - Update & Security - Windows Update - Check for updates
Microsoft Windows 11: Start - Settings - Windows Update - Check for updates
Apple macOS: Apple menu - System Settings - General - Software Update
Microsoft Office: Open an application (e.g. Word) File - Account - Update Options - Update Now
Adobe Acrobat: Help - Check for Updates
Google Chrome: In the top right, click the three dots - Help - About Google Chrome
Microsoft Edge: In the top right, click the three dots - Help and feedback - About Microsoft Edge
Firefox: In the top right corner, click the three lines - Help - About Firefox
Zoom: In the top right corner, click on your profile icon - Check for Updates
It is also important to have good backups (preferably stored away from your computer) and use strong unique passwords for each system or online service. Scan your machine every month with a third party online anti-virus scanner (a few are listed in the Resources chapter at the end of this eBook) in case your own anti-virus has been compromised. Odds are you probably won’t get a virus due to bad luck, but millions of people play lotteries with worse odds and there is always a winner.
Index or next chapter ....

