Internet Security Fundamentals - Online Edition
2 Viruses & Trojans
On the internet there are untold numbers of malicious software programs (malware for short) known as viruses, trojans, worms, botnets and spyware, but where do they all come from and why are they there in the first place?
Viruses were originally written by IT experts and transmitted by floppy disk. They were mainly malicious (deleting files, etc.) but there was no financial gain for the writer. Today, viruses are still written by IT experts and also from DIY virus kits that need little or no knowledge, but it’s mainly about financial gain. The internet allows viruses to be spread all over the world to thousands of people every minute, whether through websites or directly via email. Trojans are a specific type of virus that may either pose as something else or stay hidden on your computer, carrying out malicious activity in secret, hence the name based on the story of the Trojan horse. Trojans, worms, these are just names and types of viruses, knowing about them in detail doesn’t really help. The same way that knowing about the particular breed of dog that just took a bite out of your leg, isn’t very helpful. The important bit is avoiding the situation that led you to get bitten in the first place.
A whole industry is based on protecting you from all these nasty aspects of the internet and while they do a good job, they are far from perfect, with 90% success rates considered extremely good. That still leaves 10%, which when you consider the hundreds of thousands of viruses that exist, that’s still quite a lot. Understanding a little bit of the dangers though, will help you avoid them. Which is where this book comes in, because antivirus software has a very big weak point, namely the people sitting in front of the screen! The same way that the most sophisticated alarm system and door security is not much use if you open the door from the inside to let someone in.
If you are unlucky enough to have been infected with a computer virus, only antivirus software can help and someone who knows what they are doing. I cannot stress how important antivirus software is, as well as good backups. Even if you are using a Mac, good antivirus software stops you getting infected in the first place.
Throughout this book I will show you examples of actual virus emails that have been sent to me personally, so you can understand the lengths some criminals will go to try to get their malicious software installed on your computer.
Below we have a typical payload-based email virus. Here everything that is needed to infect the computer is included in an attachment in a compressed zip file.

The zip file will contain a virus as well as taking you to a website to enter your account details. Remember, no bank will ever send you files this way, so don’t try to open it out of curiosity.

Most viruses now arriving by email include a web link to the malicious content rather than an attachment to make it harder for antivirus software to filter out. Using a web link allows the virus writers to adapt and modify the malicious payload they wish to deliver, at any time. The link will appear at first glance to be genuine, though hovering over the link will often reveal that it points to a completely different location. If a link is not revealed, you can normally right-click and copy the destination address. Paste the address into a basic text editor to see where the link actually goes. Now this doesn’t work if a web address (URL) shortening service like bitly.com is used, which can mask any website link, e.g. it can take a long web address like this: http://www.bbc.com/future/story/20150327-gemini-nasas-unsung-hero and turn it into http://bit.ly/Gemini2015
If you receive a shortened URL, don’t follow it, instead quickly check where it goes using a website like http://www.checkshorturl.com or https://www.virustotal.com
Instead of using a link, virus writers can also include a website HTML file as an attachment or inside a compressed file. Your computer recognises the file as an internet file and will automatically open it in a web browser if you click it. The attached website file will typically take you to a malicious website or one that will try to trick you into giving away sensitive information. Here’s an example of a malicious email containing a HTML file attachment:

This email is claiming to be someone’s resume or CV.

It has a compressed zip file attachment named ‘Randal Randall – My resume.zip’ which contains a file ending in JS. This is s JavaScript file, a programming language for the internet, which greatly extends what the malware writer can get your internet browser to do.

I also received this with the JavaScript file extension put after a Microsoft Word file extension, so at first glance there’s a chance you won’t notice the .JS ending in the filename, which is what the criminals are hoping for: Randal Randall – My resume.docx.js

Remember to check the filename and extension of any email attachments before you open them by switching to the ‘Details’ folder view to see the file ‘Type’ column. Also, to help avoid falling for this trick, make sure that file extensions are not hidden if you are using a Windows computer. For more information on how to do this please see Chapter 26 – RANSOMWARE.
Next, we have an email is claiming to be from the bank HSBC and that they are sending me a document via a file sharing service (in this case Dropbox). At first glance the email is from @support-hsbc.com and ironically even includes security tips in the email footer.
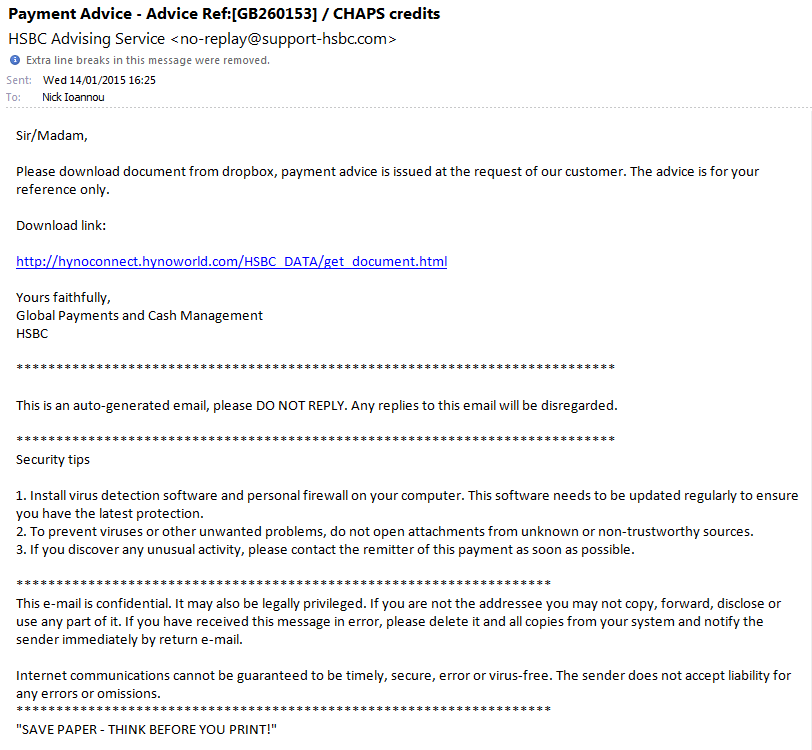
But after a closer look you will realise that this is a rather poor attempt, notice the typo in the address who the email is supposedly from (no-replay@ instead of no-reply@) and that the download link doesn’t even say Dropbox at all. For comparison, here’s a real Dropbox link:
https://www.dropbox.com/s/rdl3619l9zuehkj/Getting%20Started.pdf?dl=0
But just because it looks real, doesn’t mean it points to where it says it does. Take this link www.google.co.uk which actually goes to www.yahoo.co.uk. So be cautious about anything that wants you to download something.
Next, we have a fake email invoice for the cloud software company NetSuite. It was easy to spot as a fake as I’m not a NetSuite customer, but 16,000 businesses are. Many people receiving this email will click on the link to check the invoice as a matter of routine. The email isn’t actually from who it says it’s from as this is easily forged, so get into the habit of querying every link before you click it, or avoid using them altogether.

Here’s one claiming to be an incoming fax by the eFax service.

The view this fax link actually sends you to a zip file at dvddraco.com.ar
Some viruses go to great lengths to convince you that they are genuine and are not easy that easy to spot. Here are some of the tricks they may use:
- attachments that include your full name in the filename
- only your name in the To field
- your name at the top of the email (e.g. FAO / Dear ……)
- a mix of genuine links as well as fake ones
- unique and plausible reference numbers
- an email footer from a real business (the example below is from an actual solicitor)
- unsubscribe links
- valid customer support numbers and email address
- a hook that is relevant to you – something that needs urgent action to convince you to open the attachment or click the link (the example below is a notification of a pending direct debit for the UK Land Registry)

Example subject lines in malicious emails
I have received emails with the following subject lines, all are real, none these have been made up. As you can see, they tend to be about money, like an invoice, receipt or transaction, a delivery order, or something legal like a court order. All are designed to trick you into opening the attachment or clicking the web link, so if you receive anything similar, assume it is fake and treat it with caution.
- Unpaid Bill for Car Repair Service 3F3E
- Courier was unable to deliver the parcel, ID000220854
- Bill N-27126D
- Requested receipt ID:BCF85C
- CCE29032016_00087.jpg
- Notice to appear in Court #000166004
- Unable to deliver your item, #0000425579
- Your order has been despatched
- Contract ID 03659 has been terminated
- Voicemail from 07730881627
- FW: Statement S#174177
- Your account ID:93496 has been suspended
- Invoice JHINV40273 from Tip Top Delivery
- SCHRODER UK MID CAP FD PLC - Order Number
- SANTANDER UK PLC - Order Number 86984/126063/80 status updated to order processing
- Insufficient Funds Transaction ID:26879662
- AT&T Broadband Service Plan Price Increase -- April 2016
- Credit details ID: 06824749
- Blocked Transaction. Case No 23390003
- GreenLand Consulting � Unpaid Issue No. 74878
- Problems With Your Order - Customer ID 19177744
- Order 1307605 (Acknowledgement)
- RE:RFQ6030384 New Order
- Past Due Invoices
- ATTN: Your Invoice is attached #M9 from Nick Morris
Many email viruses actually appear to have come from a legitimate email address (normally from a government department or major company) but is actually using a forged sender address, which is known as email spoofing. In the example below, only my name is in the ‘To’ field and it seems to have come from web-filing@companies-house.gov.uk. The only clues to this being fake are the links are which take you somewhere completely different and the enquiries email has a minor capitalisation error. The telephone number and address are real, though.

Or this one that is supposedly from the UK Ministry of Justice, complete with a zip file attachment and once again only my name in the ‘To’ field.

Unexpected official looking emails that you would normally expect to arrive by post or a courier, are normally fake. Do not follow any links or open any attachments. If you are unsure, do an online search for the contact details of who the email is claiming to be from and contact them to verify if they have sent you something.
If you believe an email contains a virus or link to a virus, delete it straight away. If you leave it on your computer, or in your hosted email system, there is always a chance you or someone else may open it at a later date.
Take a look at these two emails, one of them is real. Can you tell which?


The sender’s email, subject line and wording are identical in both emails (they only look different because they were sent to two different email systems) so at first glance they are identical. The only difference is the attachment, one has a PDF file, while the other contains a compressed zip file. The genuine one is the PDF; the zip file contains a virus. This shows you how easy it is for the criminals to make their fake emails look exactly like the real ones, from the sender’s email address down to all the text and images in the body of the email. The cyber criminals have a wide range of options available to them to send you a virus via email. They can include any of the following:
- the virus program as an attachment
- a malicious web link in the text of the email, or as an attachment
- a Microsoft Office file (word, excel, etc.) attachment with malicious macro scripts
- an Adobe PDF attachment with malicious links or functionality
- a legitimate link to an online collaboration file share containing anything from this list
- a compressed file attachment that can include anything from this list
- another email message file (msg, eml) that can include anything from this list

In general, be wary of any emails containing a compressed zip file attachment. Zip files are really only meant for packaging up multiple files and compressing large files. There is very little reason for any official emails from an organisation or service to contain a zip file. The same is also true for files ending in .exe .com .msi .cpl .pif .js .scr and .bat which are program or script files. These file types may also be inside compressed zip files to try to hide their true nature.
The full list is quite long and includes: .app .arj .bas .bat .cgi .chm .cmd .com .cpl .dll .exe .hta .inf .ini .ins .jar .js .jse .lnk .msi .ocx .pcd .pif .pl .py .reg .scr .sct .sh .shb .shs .vb .vbe .vbs .vbx .ws .wsc .wsf and .wsh for Microsoft Windows operating systems.
One trick to look out for is a password protected zip attachment, which prevents any antivirus software from scanning it. The password is often in the body text of the email or arrives in a second email. Passwords can be added to zip files very easily using a wide range of free software, so just because it has a password it doesn't make it official. Also, it is worth noting that there are many forms of compressed file types, zip is the most common, but you may encounter .rar .arj .tar .lzh .7z and many others.
Passwords can also be added to many file types before they are added as attachments. Take this email which included a password protected Word file attachment and the password to open the file in the text of the email.


On opening the Word file many people would be tricked into enabling macros to run, allowing the virus to install, in fact all the text in the file is fake. Remember, just because you see a Microsoft logo when you open a document, it doesn’t mean it is real.
If that wasn’t bad enough, Remote Access Trojans (known as RATs) are also an increasing problem for many people, for as well as stealing logins, passwords and documents, a whole marketplace has sprung up selling video footage of people that was taken by their own webcam or laptop without their knowledge. The criminals then sell this footage or use it for extortion, with prices as low as $1 per video for footage of women. Any recording indicator lights on a webcam are turned off by the Trojan, so there is nothing to alert the victim to the fact that they are being recorded. These Trojans can remain hidden on victim’s machines for months or even years, without the user having a hint of suspicion.
My advice is to turn webcams to point to a wall or down to the table when you are finished with them, especially if they are used in a bedroom. For laptops with built-in webcams either close the lid or carefully cover the lens with something that leaves no residue or marks. Some laptops even have a built-in lens cover for the webcam, look for a small slider just above the webcam.
A compromising personal video can be used to extort further video footage or money in return for deleting them afterwards, but this is nearly always a lie, and the situation can spiral out of control rapidly. If anyone ever contacts you about having videos about you of a sexual nature, immediately contact the police. Never agree to meet the person or expect them to hand over the ‘only’ copy in return for anything. The same applies for the criminals offering a ‘fix’ to remove the Trojan, via a small utility program.
If the infected machine is part of a corporate network, this allows the criminals to launch further attacks to gain access to other machines and eventually the main servers. A Trojan can also record any user activity including keystrokes and screen footage, so personal online accounts are quickly compromised as well as business related internal and online systems. All this information is transmitted to online servers controlled by the criminals and may held for months before it is acted upon or sold on to other criminals.
Index or next chapter Vulnerabilities & Security Flaws


