Internet Security Fundamentals - Online Edition
8 Phishing - part 2
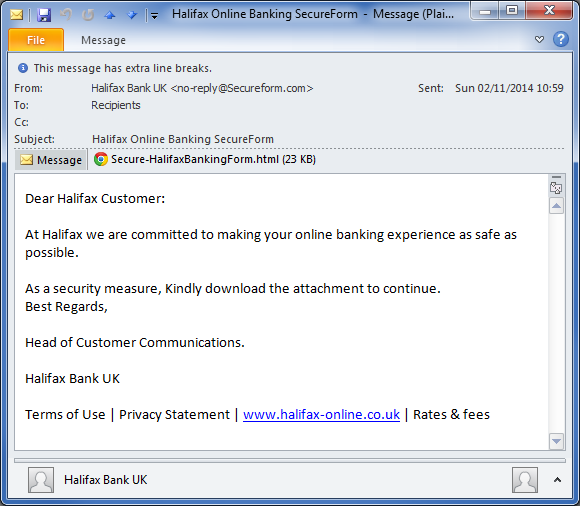
Now not all phishing attempts are complicated or advanced. Some are very basic, so basic they get through Microsoft’s Office 365 malware filters like this email claiming to be from the Halifax (a division of Bank of Scotland plc) that contains a HTML form as an attachment. The form opens in your browser and all the images are pulled directly from Halifax’s website to make it look genuine. There is nothing malicious, just a form to fill in asking for all your personal and banking information, together with a submit button which emails everything to resultboxes101@gmail.com

Password recovery is also being targeted for users of Gmail, Outlook.com/Hotmail and Yahoo Mail email services by criminals, with the goal of taking over the account by changing the password. The scam involves little tech knowledge by the criminal and all they need to know is the targets email address and mobile number. All of these services have a feature that if a user forgets their password, they can request a new one once they provide a validation code that is sent to their mobile to prove that they are who they say they are. What the criminals do is enter the victims email address into the ‘I’ve forgotten my password’ area of the sign in page and select to send a SMS text message with the validation code.

The next bit is key, the criminal then sends another SMS text message from their mobile to the victim’s mobile claiming to be from the service provider on the lines of: ‘Unusual activity has been detected on your account. A verification code has been sent to this device, please reply with validation code otherwise your account will be blocked’ or ‘…….. has detected that your email account …@… has been flagged due to suspicious activity. Please respond with the code that was sent to you in the past 5 minutes.’
If you fall for this scam, the criminal can then take over your account and any related services by changing your password. Often after adding a forwarding address to make a copy of your emails, they may send you another SMS text such as: ‘thank you, your new ‘temporary password is …...’ in order to hide their true intentions. The best way to protect yourself from this scam is to mistrust all SMS text messages, unless you have specifically requested one from a service provider.

How many things can you spot in this phishing email that are not quite right? There are at least 3, the From address, the To address and the missing image in the footer.
What about this one? Other than not being from natwest.com and no To address?


This one just has one error, so expect some phishing emails to be perfect, but they will still be out of context, in this case, the banks never email you about security. Remember don’t trust any hyperlinks, instead bookmark these real links to manage your settings that are often phished:
- Google account: https://myaccount.google.com/security
- Apple ID: https://appleid.apple.com
- Microsoft account: https://account.microsoft.com/ or https://login.live.com/
- Yahoo account: https://login.yahoo.com/account/
- LinkedIn account: https://www.linkedin.com/mypreferences
Remember not to panic if you appear to have received a large, unexpected bill. The criminals are relying on you seeing the big number and clicking on links to clarify that it is a billing mistake.


Once the criminals find something that gets results, they then make it into a template and use it again and again. In the first example the BT Bill is supposedly from btbusiness@bt.com <btbusiness@btconnect.info> with Robert Scott as the CEO, while the second is from btbusiness@bt.com <btbusiness@bnetc.com> with Carlee Dripps as the CEO.
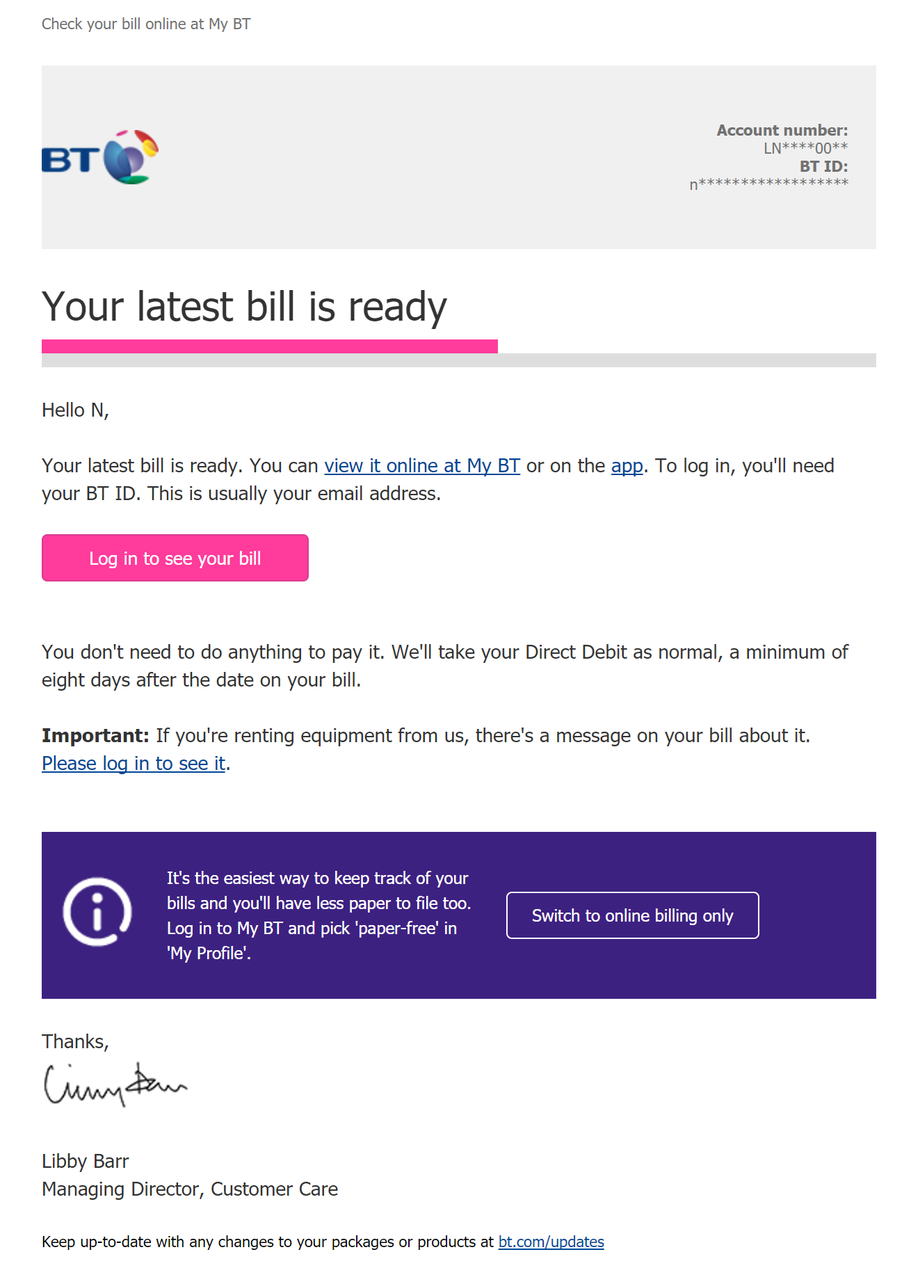
For the record, here is what a genuine BT bill at the time looked like:
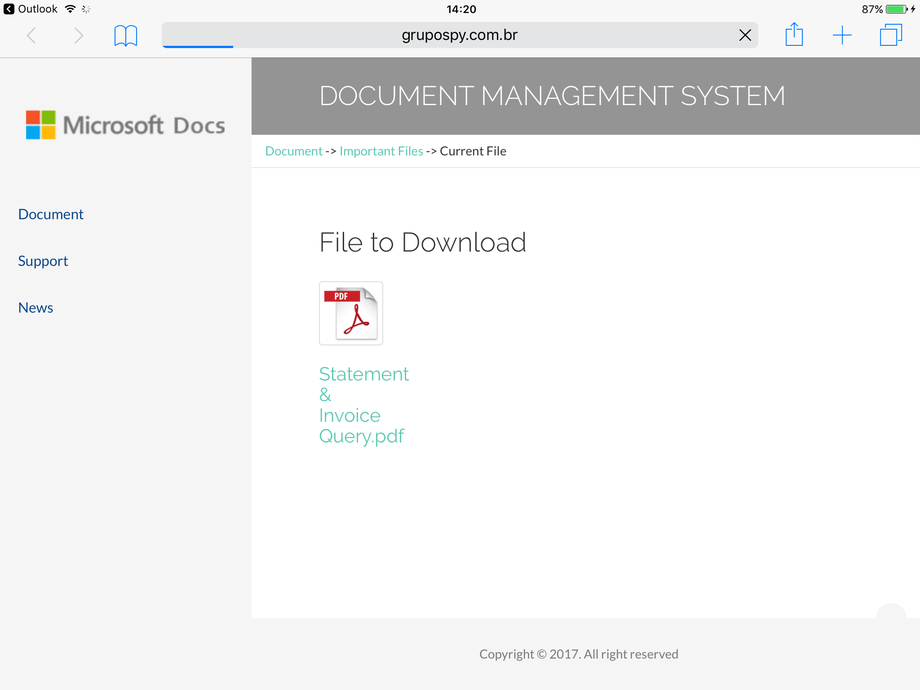
Don’t forget that businesses are also heavily targeted. Take this example which is trying to trick people into giving up their Microsoft Office 365 credentials.

There are some really well put together phishing emails doing the rounds, like this one claiming to be from a web domain registrar. Web domains are critical for businesses and any issues with them can take up to 48 hours to resolve, which is why the criminals target them. A simple MX record change can route all company emails to the criminals before being delivered as normal. If you oversee a business web domain, please regularly check your DNS records, email journaling settings and email rules for any suspicious changes. And, if you haven't already done so, turn on two-factor authentication (see chapter 40) for your registrar account.

Cybercriminals are also using legitimate mainstream file transfer services like Dropbox, Box, Google Drive, OneDrive and many others. These services scan for malware, so instead the cybercriminals include their malicious or fake links within the document being transferred. Here is an example of a fake purchase order that has been sent via Dropbox. As you can see, the senders email address is real, it has actually been sent via Dropbox.

Clicking ‘Download files’ takes you an official download page, remember in this scenario the service being used is only checking for malware and not scanning every file for malicious or fake links. In this case, it is a PDF document claiming to be a quote.


On opening the PDF document, it appears that only a preview of the file has been opened. This is all smoke and mirrors, the PDF has been created to specifically look like this, with the intention of getting you to click the ‘VIEW DOCUMENTS NOW’ link. So, you can see the levels of ingenuity the cybercriminals are willing to go to in order to get you to follow a link and enter the information they are after.
To sum up, if you think you may have fallen for a phishing scam, immediately contact your bank or credit card provider. Change any account passwords that may have been passed to the criminals ideally using a smartphone (rather than your computer in case it has been compromised) and contact the service provider. You will also need to change any online services that use the same username and password combination. Next inform the police, in the UK it’s ActionFraud, the national reporting centre for fraud and cybercrime, at https://www.actionfraud.police.uk/
If you were using a computer when you were tricked, assume it has been infected, and stop all online financial activities and anything that needs a password on that computer. Jump to the ‘Removing a Virus’ chapter and check that nothing is on your machine that could cause further problems. Remember, question everything and everyone afterwards, especially if you are called by someone from an organisation you haven’t told, that now knows you have been phished. They may be the criminals coming back for more, asking you to confirm bank details as they have seen suspicious activity or something similar.
If your email credentials were phished, you will also need to inform your friends and family that they might get emails claiming to be from you and not to open any attachments or follow links. You might want to send a message via a text or a phone call, as not everyone checks their email with the same regularity.
For stuff that didn’t manage to trick you, and if you feel confident enough to, you can report fraudulent links and email addresses to the online services and companies that the cyber criminals are using. As a result, they get flagged and blocked, saving others from being potential victims. See the Resources section called ‘Reporting Fraudulent Links and Emails’ for the various ways you can report phishing emails.
Index or next chapter Fake Antivirus
Please support this website


