Internet Security Fundamentals - Online Edition
8 Phishing - part 1
The term phishing is used for the various ways cybercriminals attempt to trick us into parting with sensitive information such as login credentials, financial details, personally identifiable information (PII) as well as medical information and business intellectual property. According to a report from the security firm Sophos, 89% of phishing attacks are carried out by organized crime, with billions lost every year to phishing. That is a lot of money, which is why the problem has grown exponentially, with Google Safe Browsing registering over 2 million phishing sites as of January 2021. Fast forward to 2024, the Google blog (https://blog.google/products/chrome/google-chrome-safe-browsing-real-time/) states ‘Safe Browsing assesses more than 10 billion URLs and files every day, showing more than 3 million user warnings for potential threats.’ While not all cybercrime is due to phishing, it plays an integral part in its overall effectiveness, leading to identity theft and fraud.
Here is a typical phishing email so you divulge a username and password for online banking.

The ‘Click here to read’ link actually goes to: http://www.hsbc.co.uk.171035a6u.net/1/2/HSBCINTEGRATION/CAM10/jsessionid4444yrRAixoA81U9REEStz1I3n_19ko2y9r3_IDV_URL_hsbc_MyHSBC_pib/index.php
The http://www.hsbc.co.uk looks normal but the important bit is 171035a6u.net which is where you are really going.
Phishing for personal info and login details is often combined with other malicious software, like a trojan. Most online security systems were originally based on the old telephone banking security model, where information like your mother’s maiden name was hard to come by. Social media websites like Facebook have changed all that and can often be used to fill in the gaps from a phishing scam.
With enough personal information, it is possible to get hold of a birth certificate copy and from that open bank accounts and take out loans, all in someone else’s name. You can see why phishing is big business on the internet.
A common phishing target is your email password for common web hosted systems like Hotmail/Outlook.com, Gmail and Yahoo Mail. Emails are sometimes also timed to coincide with events in the news about issues the email provider may be having (which may not have actually affected you) and can look very convincing like the fake one below, from an account named: Outlook Administrator <messagecenterdettbss@outlook.com>:

The clue in this fake email was that fact that the ‘Verify Now’ button didn’t go to a Microsoft web address but rather: https://dl.dropboxusercontent.com/s/nq0p005x8h42sxf/com.docx.html
But this is quite easy to miss if you are reading emails like this on a small smartphone screen.
So, what can you do to protect yourself? The internet works by looking up every web address you type or click a link to by contacting a special computer called a domain name server or DNS for short. This DNS service is normally provided by your Internet Service Provider (ISP) but you can often change it to another system which provides filtering for websites that are known to be malicious or fake. OpenDNS and Quad9 both provide FREE phishing protection, see: https://www.opendns.com/ or https://quad9.net/ Please understand that this is ‘increased protection’ not total protection, the same way that a motorcycle helmet protects you on a motorbike. OpenDNS is covered in more detail in chapter 35 on Parental Control Software.

If anything looks even slightly suspicious, close the browser. If you’ve entered passwords into a page that you think may have been a phishing site, locate another computer you trust and try to change your password ASAP.
Here is another dodgy email; it was easy to spot as I’ve never been an Orange customer:

The link takes you to http://web.orange.universitube.com.br/r/login which is nothing to do with Orange. Remember, service providers never ask you to validate your credentials via an unexpected email and they generally know who you are and refer to you by name. Change your passwords at least once a year to strong phrase-based passwords sprinkled with numbers and capital letters, which are easy to remember but not in any dictionary. For example: L3Tmeinrightn0w
The one area that needs special mention though is the ‘tax rebate’ email. This type of phishing scam casts a very wide net, because while you have a choice of where you bank or which mobile phone company you use, each country only has one income tax government department (normally held in dread). So, when you receive an email saying you’ve overpaid and are owed some money back, some are quick to follow the link. Here is one I recently received:

The link takes you to http://www.xaydungvietgia.com/js/file/backup/HMRC/Portal.html
Notice the missing space typo and the fact that there is no name, reference numbers, etc. This is a poor attempt, but together with profile building from social media and previous phishing results, a targeted email with genuine details is possible. Best always err on the side of caution and contact your accountant or the relevant tax department by telephone (don’t use any numbers in the email) to confirm any genuine refunds.
Here is another one, though this time the second link to HM Revenue & Customs is genuine, while the main link is fake.

Even if the email has your correct name and email address, it is likely to be fake. Best to always err on the side of caution and contact your accountant or the relevant tax department by telephone (don’t use any numbers in the email) to confirm any genuine refunds.

Instead of offering a refund, this fake HMRC email above is trying to scare you into thinking you owe them money, a lot of money. Even if you know you don’t owe the government or an organisation money, mistakes do get made and it is human nature to want to make sure your credit rating is not affected by a mistake. The important bit here is not to panic, just because an email says you owe money doesn’t mean it is real, in fact chances are it’s not real if it is tax related. Any genuine correspondence would have your tax reference number to start with, as well contact numbers, etc. Though, even if there are contact numbers, these could fake too, so avoid any links and telephone numbers and do some research online to find the department you would need to contact. Also, be aware of bogus bailiff emails claiming to be from legitimate companies, telling you they are chasing an outstanding debt. Once again, contact the company who the debt is for directly, rather than trust anything in the email.
Online shopping is also a big target, with emails supposedly from many major brands and online retailers. Here’s one from an online clothing retailer:

The link takes you to http://www.mpcs.ac.th/mpcsweb/plugins/editors/backup/very.co.uk/login.htm which is a website address in Thailand.
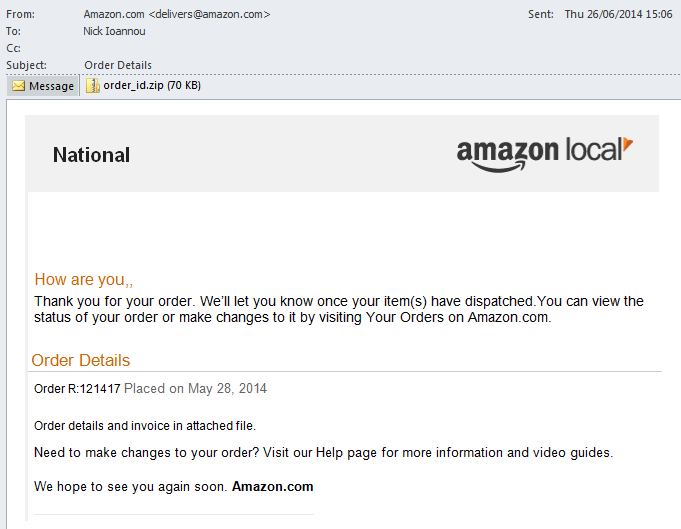
The previous Amazon confirmation email containing a zip attachment is fake, while the one below is genuine. Be wary of any confirmation emails with attachments, especially ones that contain yet another email and compressed zip attachments.

The vast number of people that have Amazon accounts makes them a huge target, so much as that the criminals create clones of the Amazon Billing Center to try to glean not only your Amazon credentials, but also your address, date of birth, mother’s maiden name, bank account and credit card details. To get you to visit these fake websites the criminals use a variety of emails asking you to confirm or update your details, like this one:
Your Amazon.co.uk security check failed
Message from Amazon.co.uk to customer registered with email address: "info@booleanlogical.com"
Greetings from Amazon.co.uk,
Your card payment profile security check could not be completed.
A card provider will often decline an attempt to charge/verify a payment card if the name, expiry date, or postcode you entered does not exactly match their information. Valid payment information must be received within 2 days, otherwise your account will be cancelled.
Please follow the link below to resubmit your correct payment details.
We recommend you select an option to create a new payment method when prompted and enter the complete information for the payment method you wish to use.
Clicking the link takes you to this fake Amazon Billing page.

Below, we have a typical ‘we tried to refund your credit card’ phishing email where they try to get you to enter all your credit card details in order to get the so-called refund. This one is not very professional and full of typos, but some can look very genuine. More sophisticated versions of this scam will target businesses with products and brands typical to their sector.
Dear Customer
A technical fault at one of our software manager accounts receivable abbey mara because unfortunately the imputed amount 985.50 Euro on your credit card. In order to repay this sum used in error on your account, and in the shortest delays, please log onto the link that appears below this message.
Click here to access your sheet special refund.
Thank you for your understanding and we apologize for the inconvenience.
Have a look at this email claiming to be from support@tvlicense-refunds.co.uk

Clicking the ‘Online Application Form’ takes you to a very convincing fake website:

Which then goes on to ask for your address, bank account info, credit card and a password.

There are now even phishing emails based on fake online takeaway restaurant delivery confirmations. Basically, you receive an email in the early evening confirming a pizza delivery and you naturally assume it must be a mistake. There may be an ‘order details’ button which may either take you to a website or get you to download something. If the sender knows both your email address and physical address, this can be made into a very convincing email, which will easily fool most people. The thing to remember is that a lot of online takeaways expect payment upfront by credit card, so even if someone did order something by mistake, just ignore it.
The latest phishing scam doing the rounds is the ‘Account Info Change’ or ‘Updated Information’ email or mobile text message. It is an update confirming that security information such as your address or account security question has been recently changed as per your request. Peoples’ first reaction is ‘what’s going on must be some type of mistake’ and there is a handy link to inform them that you did not make the changes. Obviously, the link won’t take you the real account login page. You may have noticed that many phishing emails look very similar, as if they have been created from a common set of tools. These tools will evolve though over time, so expect the fake emails to get harder to spot.
Every year more services we use correspond via email (mainly to save costs) and we sign up to new digital services that may not have existed a few years ago. This adds to the list of companies and services that criminals can claim emails to be from. Premium paid for streaming services for music, TV and films are now a target, with fake security validation email requests or account terms update confirmations.

Here a fake BT phone bill is claiming that a regular payment failed and that you will lose service unless rectified.
Now, have a look at this fake email claiming to be from the Netflix service with a link to: http://netflix-user.net/validation_code=2382492chwcb398u3hff20ucwucg3ch9wcj3ch/
At first glance the netflix-user.net appears to be legitimate, but it is bogus and has nothing to do with Netflix. Look out for variations of a company’s domain name as most are fake.

But not all fake Netflix emails are as easy to spot. Take this next one supposedly from support@mailer.netflix.com claiming that your account is on hold and that you need to validate your billing and payment details. You’d think that they would at least know your name if you had problems paying them! Anyway, hovering over the ‘Validate Membership’ link goes to: https://user.netflix.information-features-necessary.com/ which seems plausible, but unfortunately will land you with a huge headache, if you hand over your Netflix password, credit card and address details.
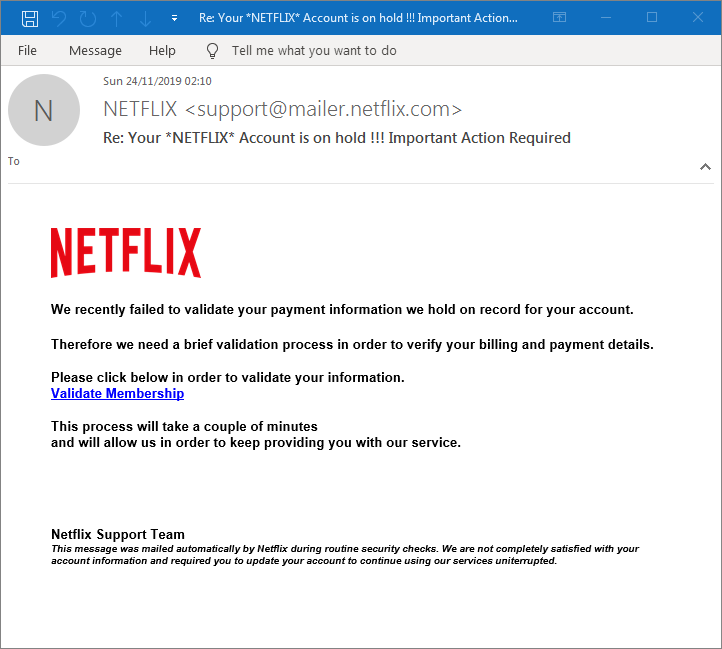
Remember, it is easy to fake a sender’s address in an email, so if you are not sure based on where any links seem to go, ignore the link and instead, manually type the main website address either from memory or an online search, ideally from a saved favourite in your web browser.
Sometimes the emails will be more personalised and contain your email address and name in the body text to appear more genuine. They may even contain a valid account number or other information like subscription dates gleaned from data breaches and other online sources like fake surveys, referral promotions, competitions and giveaways that you may have filled out months earlier and forgotten about. It is now very easy for fraudsters to profile their potential victims if they choose to do so, which is then either used to make phishing emails more convincing or resold to other criminals.

To make matters worse, a new type of phishing email has been uncovered that contains links that actually go to the real website of the company the email is claiming to be from, rather than a fake site. If you follow the link though, clever programming creates a hidden area in your browser which captures everything you type, and this is then sent to the criminals. So, remember, don’t follow links – especially for anything to do with money and update your web browsers.
Given the wide range of online enabled services people use, such as TV streaming services and antivirus, the criminals send out their emails en masse, safe in the knowledge that a good percentage will have that service, like the following fake Disney+ and McAfee antivirus emails.



Take this fake BT phone refund email which asks you to complete the claim via a link. Whereby you are taken to a fairly convincing fake version of BT’s website to enter your email address and password. The criminals can then ask you to confirm your banking details before automatically logging you in to the actual BT website, leaving you none the wiser.

So, to give you an example of the lengths some criminals go to in order to fool you, have a look at these BBC Health websites. One of these BBC News Health websites is fake; can you guess which at first glance?


The first one is fake; the second one above is real.
Index or next chapter Phishing part 2


