Internet Security Fundamentals - Online Edition
32 Data Breaches
Recently the way some major companies realise they have been a victim of a data breach is by a large number of their own customers alerting them to the fact that they have been defrauded. Their customers fell for a scam because the criminals had access to information that only the genuine company would know. Some of these scams are telephone based, some email based, possibly both, which are made to seem official using the stolen information about the customer. This information can be contact details, customer account numbers, account passwords, renewal dates, previous order history and anything else the company may record about their customers.
Some scams are even based around the fact the company has suffered a data breach, with criminals sending out fake password reset emails or calling to change the credit card against the account. So how does a company get hacked and all the customer data end up in the criminal’s hands? It can be from a wide variety of methods ranging from a company insider, suppliers or subcontractors that have been compromised, phishing emails leading to remote access Trojans, targeted attacks against staff so that they visit malicious websites hosting exploit kits, virus laden USB memory sticks left where staff are likely to pick up, the list goes on. As a customer it is now a good idea to assume all communications from a company made to you are possibly fake, whether over the telephone, SMS text, or by email.
If someone telephones you, saying they are from a certain company you use and before they can proceed, they need to verify your identity, stop don’t answer them. How do you know they are genuine? Before I used to challenge them to tell me something to prove who they were, but now that the criminals may also have that information via a data breach, I need a different approach. I now tell them that I have no way of verifying who they are, therefore please could they give me their full name, company and department, so I can call them back. I specifically do not ask for their telephone number and ignore it if they give it, as it may be false. Instead, using whatever internet capable devices are available, I go to the company’s website and find their contact details. Now if the caller was genuine, you will eventually (depending on the queuing system) get through to the person that called or someone on their team. If there is no one by that name you were given or no notes on the system for the company to call you, then it was probably a fake call.
The same goes for emails from any company, first assume they are fake, then try to establish whether they are genuine. If there are prominent links to verify or reset your account, which you hadn’t requested a few minutes before, ignore them. Carefully hover over links and see if they are genuine, read the full path as fake links may include the company name. If you think it might be official, still don’t click it. Instead, open a browser and type in the company’s website and log into your account. There will normally be a notice if there is a need to reset your password. If you hear in the news that a service you use was hacked, don’t wait for an email to tell you to reset your password, login manually and reset it yourself. Often data breaches are bigger than they first appear, so resetting your password is the safest option.
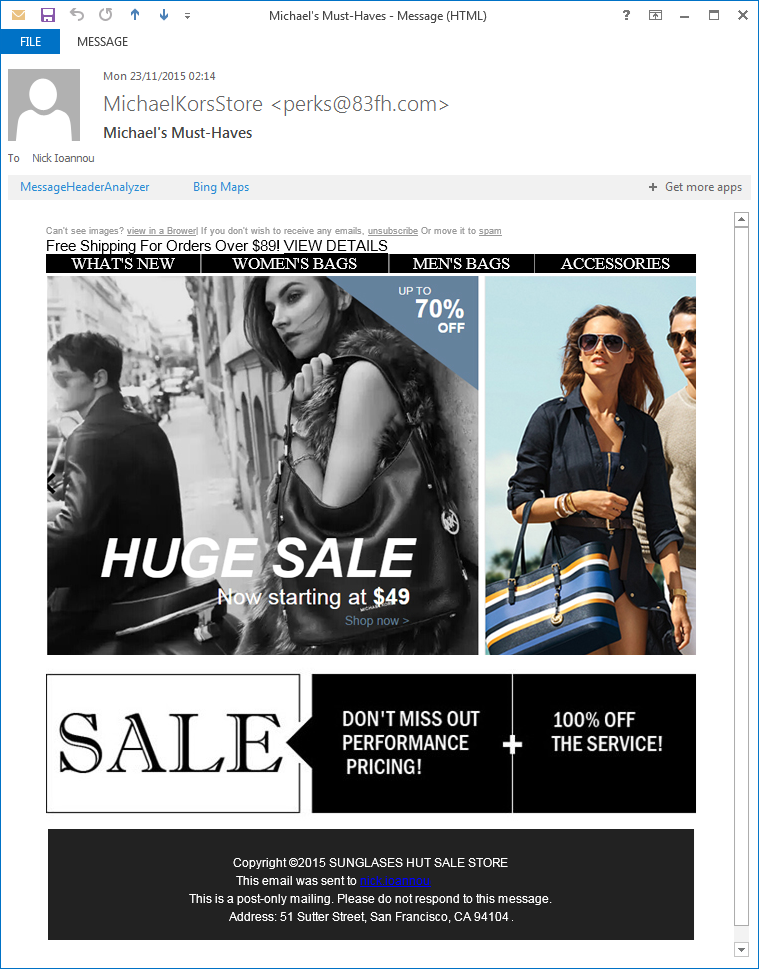
This email advert is actually fake. The criminals have lots of options to use the information they have on you; it doesn’t always have to be password resets or account verification. Clicking any of the active links in this email would have taken you to a malicious website.
Index or next chapter Alternative Operating Systems
Please support this website